HackTM_CTF_2020
HackTM_CTF_2020 was the first edition of HackTM CTF.
The event consists of 2 rounds: the Qualifying Round and the Final Round.
The Qualifying Round is a 48h long Jeopardy CTF. Following this, top 10 teams from the scoreboard qualify for the Final Round which takes place in Timisoara, Romania, during the HackTM hackathon.
Unfortunately, this year's Final Round was organized online due to the restrictions.

HackTM_CTF_Quals
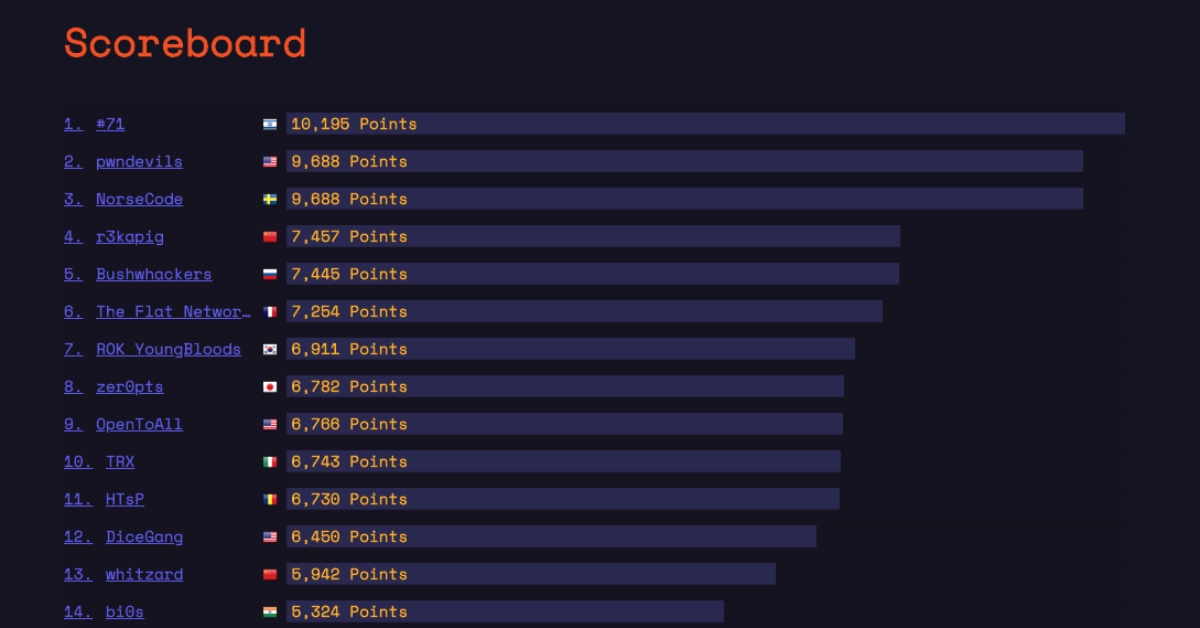
*** https://ctftime.org/event/956 ***The Qualification Round took place on February 1-3 2020 and it featured tasks in a variety of categories: pwn, web, rev, forensics, crypto, misc, and osint.
For this round I created 4 challenges:
|
1. Obey The Rules |
|
445 Points, 35 Solves |
|
2. OLD Times |
|
424 Points, 41 Solves |
|
3. Merry Cemetery |
|
496 Points, 10 Solves |
|
4. Think twice before speaking once |
|
491 Points, 14 Solves |

HackTM_CTF_Finals
*** https://ctftime.org/event/1140 ***The Final Round took place on December 12-14 2020. The 10 finalist were:
📢Finally, after a long period of decision making, we are happy to present to you the 1⃣0⃣ finalists of the HackTM CTF competition. On December 12, these teams will participate in a virtual final (https://t.co/SxX32K2XxJ). Stay tuned! pic.twitter.com/epwuHDkrXH
— WreckTheLine (@WreckTheLine) September 21, 2020
The challenges that I created for this round were:
|
1. MobaDEX |
|
428 Points, 4 Solves |
|
2. The Man, The Myth, The Legend |
|
428 Points, 4 Solves |
Through the MobaDEX challenge I tried to introduce an idea that I didn't really meet at CTFs.
MobaDEX is an Android Messaging Application designed similar to Snapchat. It implements 5 main functionalities: Register / Autenthicate / Add Friend / Write Moba / Read Moba.
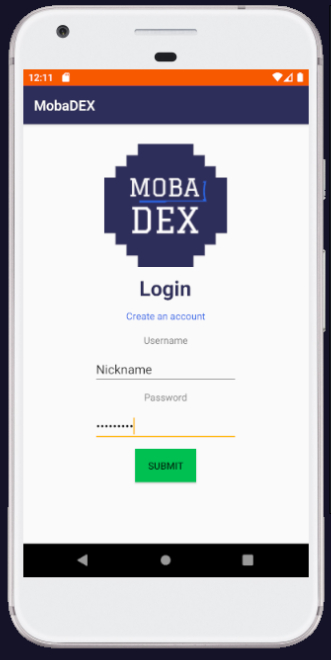
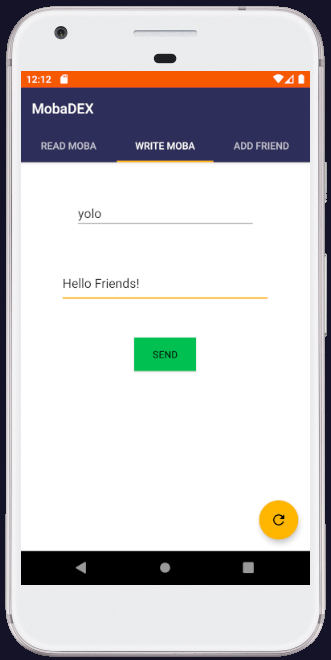
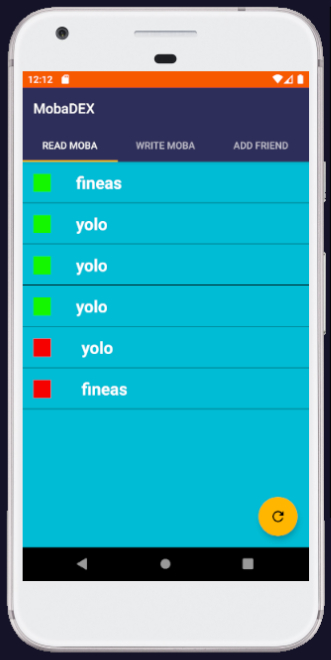
The idea of the challenge was to find a way to get the flag from the Admin's account.
The intended solution for this was to abuse the fact that the SendMoba Activity was exported which would allow the attacker to send Mobs to users which were not on his Friends List (for example the Admin).
The payload had to be crafted in such a way that when the Admin reads the Moba it will trigger the exploit, read the flag, and send it back to the attacker which could read it as a normal Moba.
Here is a POC:

A more detailed writeup can be found at: https://github.com/Fineas/Me-CTF/blob/master/android_challenges/challenges/MobaDEX/README.md
Only 4 teams managed to solve this problem during the competition. You can read their writeup at: ROK YoungBlood, zer0pts, TRX, r3kapig

Concluding
Looking back, organizing this edition of HackTM CTF was amazing. Although it was a bit difficult to balance work, university, CTFs and writing the challenges,
I would like to thank my colleagues without whom the competition would not have been the same and to BanatIT which supported us and gave us the freedom to organize the competition just the way we want.
Authors: trupples,
nytr0gen,
stackola,
0xcpu,
Legacy,
NextLine,
Sin__,
tcode,
Qyn,
JUSTICE.


HackTM CTF was amazing. Although it was a bit difficult to balance work, university, CTFs and writing the challenges,
I would like to thank my colleagues without whom the competition would not have been the same and to BanatIT which supported us and gave us the freedom to organize the competition just the way we want.